I participated in an AeroCTF Qual 2019 as a member of team insecure. We reached 14th place with 3411pts. Thanks to admins for a great competition.
I solved the following challenges. I'm going to describe them.
- [Warmup 100pts(23 solves)]misc_warmup
- [Warmup 100pts(47 solves)]reverse_warmup
- [Crypto 444pts (33 solves)]pycryptor
- [Forensics 470pts(21 solves)]undefined protocol
[Warmup 100pts(23 solves)]misc_warmup
description:
Our reverser loves to create various tasks. This is an example, try to solve.
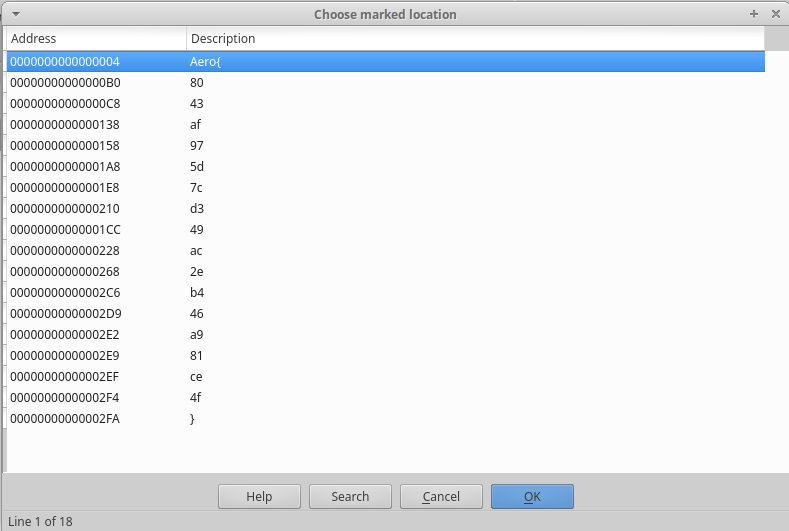
We were given a file whose name was some_idb.i64. It was generated by IDA. So I opened it using IDA and viewed comments by shortcut key C-m. Then I saw the split flag.
[Warmup 100pts(47 solves)]reverse_warmup
description:
Again, our developers are watching all kinds of memes. Now use for this some program. Try to crack this soft.
The given file just_a_meme.exe is a PE32 file which was written by Go. I analyzed it statically using IDA disassembler. Then I found that the main_checkKey method is the core of its work. It compares a static bytes \x89w\x86\x87\xa0\x8dw\x85\x8d\x85\x8d\xa3 with the command line argument character by character, where each character is xored with 0xd and added by 0x25.
rdata = [0x89, 0x77, 0x86, 0x87, 0xA0, 0x8d, 0x77, 0x85, 0x8d, 0x85, 0x8d, 0xa3] key = '' for x in rdata: key += chr( (x - 0x25) ^ 0xD ) print(repr(key))
I entered the key i_love_memes to the binary and got the flag.
[Crypto 444pts (33 solves)]pycryptor
description:
Our programmers decided not to use that encoder written in Golange and created a new one in Python. Needless to say that we again lose our drawings? Could you look again at the encoder and an example of its use?
We were given two files: cryptor.py(here) and enc_image.png. At first glance, I found that this image was xored. As some blocks in the image were encrypted with the same key, we could remove the effect of xoring from the image. I choosed the most common block as the base image and got the "nearly decrypted" image. The flag is written at the center-bottom of the decrypted image.


[Forensics 470pts(21 solves)]undefined protocol
description:
We managed to get traffic from the machine of one of the hackers who hacked our navigation systems, but they use some kind of strange protocol over TCP. We were not able to disassemble it, maybe you can find out what he was transmitting?
We got the undefiend_protocol_traffic.pcapng which had some unknown-formatted TCP traffics. By the observation, I could guess the protocol.
I saved the pcapng file as pcap format and decoded the messages by the following script.
import dpkt import re def dec(k, s): r = '' for c in s: r += chr(ord(c) ^ k) return r f = open("hoge.pcap", "rb") pcr = dpkt.pcap.Reader(f) key = None for t, buf in pcr: eth = dpkt.ethernet.Ethernet(buf) ip = eth.data if isinstance(ip.data, dpkt.tcp.TCP): tcp = ip.data if len(tcp.data) != 0: d = tcp.data.decode() if re.match(r'[0-9]+\n', d): key = int(d[:-1]) else: print(dec(key, d)[::-1])
There was a flag at the last of traffic.
(...snip...)
iloveyou
Username:
lol
[-] Username is invalid!
Exit
qwerty1234
Username:
admin
Enter the password:
admin
Welcome admin!
Aero{94d04d04b327e4e52a0bb6c67b3fca7b}